How Zoho CRM Can Streamline Your Sales Process and Boost Revenue
How Zoho CRM Can Streamline Your Sales Process and Boost Revenue In today’s fast-paced business…
AI & Cybersecurity: How to Redefine Business Security
AI & Cybersecurity: How to Redefine Business Security In today’s fast-moving digital world, cybersecurity is…
Why SMEs Need Enterprise-Level Cybersecurity Now More Than Ever
Why SMEs Need Enterprise-Level Cybersecurity Now More Than Ever For many small and medium-sized enterprises…
IT Support Myths: Debunking the Most Common Misconceptions
IT Support Myths: Debunking the Most Common Misconceptions When it comes to IT support, many…
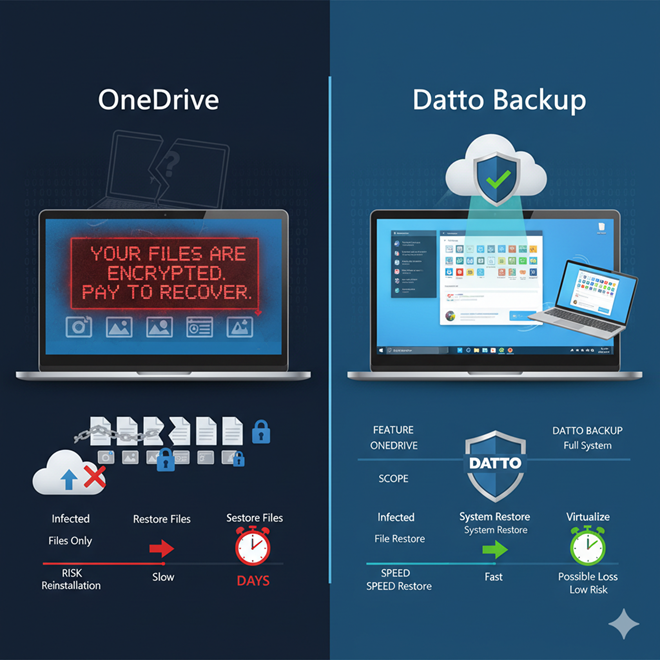
What happens if your laptop is hit by ransomware? OneDrive vs Datto Backup
What happens if your laptop is hit by ransomware? OneDrive vs Datto Backup It’s just…
Password Management: Smarter Ways to Stay Secure
Password Management: Smarter Ways to Stay Secure We have all been there: forgetting a password,…
The Hidden Cost of IT Downtime for Australian Businesses
The Hidden Cost of IT Downtime for Australian Businesses IT downtime is more than a…
Master Your Windows PCs: Updates, Shortcuts, and Performance Tips
Master Your Windows PCs: Updates, Shortcuts, and Performance Tips Windows PCs are essential for productivity,…
Work from Home Security: Essential Tips for Remote Teams
Work from Home Security: Essential Tips for Remote Teams With more teams working remotely than…